News

October 15, 2025 • 1 min read • Hackernews
Over 100 VS Code Extensions Exposed Developers to Hidden Supply Chain Risks
New research has uncovered that publishers of over 100 Visual Studio Code (VS Code) extensions leaked access tokens that could be exploited by bad actors to update the extensions, posing a critical software supply chain risk. A leaked VSCode Marketplace or Open VSX PAT [personal access token] allows an attacker to

October 15, 2025 • 2 min read • theVerge
Google will let friends help you recover an account
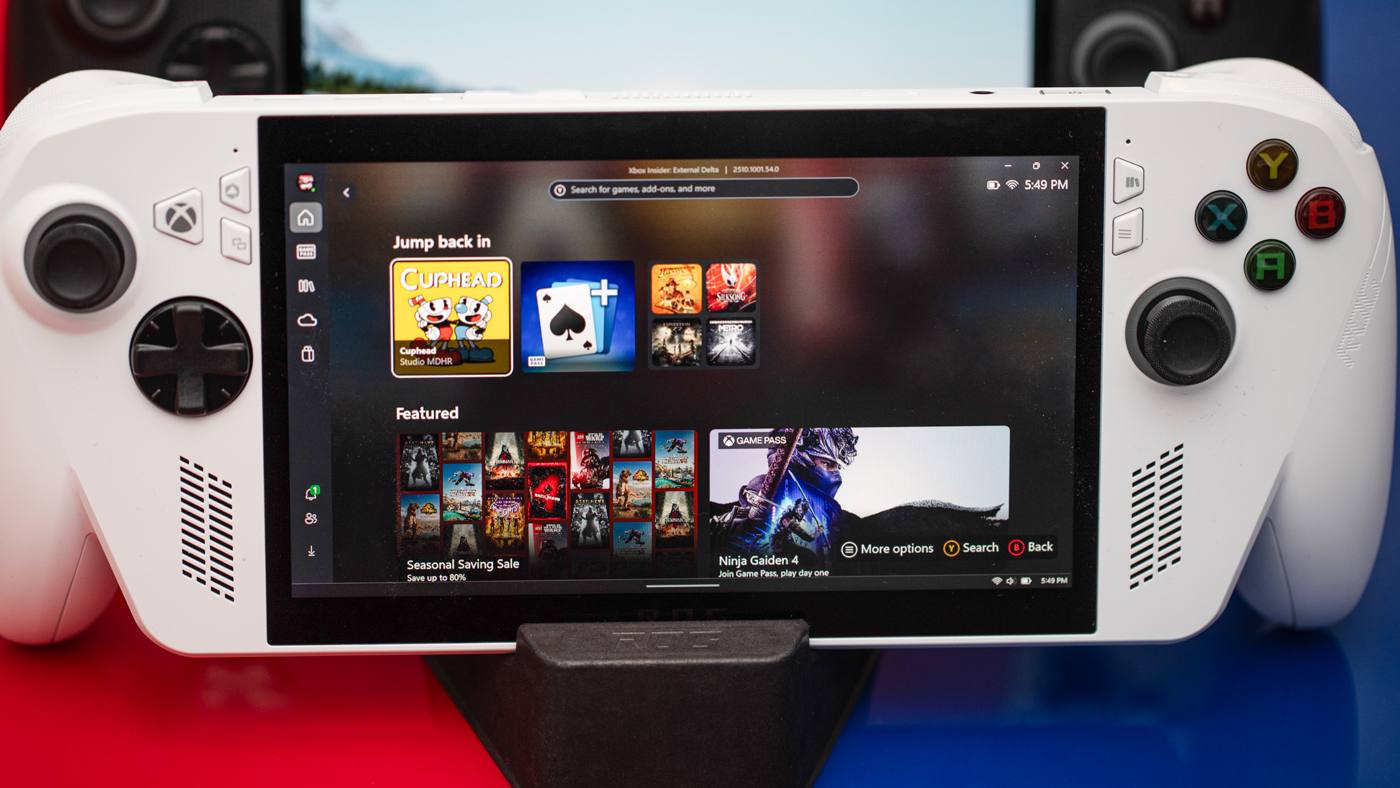
October 15, 2025 • 1 min read • theVerge
Xbox Ally and Ally X review this is not an Xbox

October 15, 2025 • 1 min read • Hackernews
How Attackers Bypass Synced Passkeys
TLDR Even if you take nothing else away from this piece, if your organization is evaluating passkey deployments, it is insecure to deploy synced passkeys. Synced passkeys inherit the risk of the cloud accounts and recovery processes that protect them, which creates material enterprise exposure. Adversary-in-the-middle (AiTM) kits can force authentication fallbacks that
October 15, 2025 • 2 min read • theVerge
These are the Office icons Microsoft rejected

October 15, 2025 • 1 min read • Hackernews
Two New Windows Zero-Days Exploited in the Wild One Affects Every Version Ever Shipped
Microsoft on Tuesday released fixes for a whopping 183 security flaws spanning its products, including three vulnerabilities that have come under active exploitation in the wild, as the tech giant officially ended support for its Windows 10 operating system unless the PCs are enrolled in the Extended Security Updates (ESU)

October 15, 2025 • 1 min read • Hackernews
Two CVSS 100 Bugs in Red Lion RTUs Could Hand Hackers Full Industrial Control
Cybersecurity researchers have disclosed two critical security flaws impacting Red Lion Sixnet remote terminal unit (RTU) products that, if successfully exploited, could result in code execution with the highest privileges. The shortcomings, tracked as CVE-2023-40151 and CVE-2023-42770, are both rated 10.0 on the CVSS scoring system. The vulnerabilities affect Red Lion SixTRAK

October 15, 2025 • 1 min read • Hackernews
Hackers Target ICTBroadcast Servers via Cookie Exploit to Gain Remote Shell Access
Cybersecurity researchers have disclosed that a critical security flaw impacting ICTBroadcast, an autodialer software from ICT Innovations, has come under active exploitation in the wild. The vulnerability, assigned the CVE identifier CVE-2025-2611 (CVSS score 9.3), relates to improper input validation that can result in unauthenticated remote code execution due to the

October 15, 2025 • 1 min read • Hackernews
New SAP NetWeaver Bug Lets Attackers Take Over Servers Without Login
SAP has rolled out security fixes for 13 new security issues, including additional hardening for a maximum-severity bug in SAP NetWeaver AS Java that could result in arbitrary command execution. The vulnerability, tracked as CVE-2025-42944, carries a CVSS score of 10.0. It has been described as a case of insecure deserialization. Due

October 14, 2025 • 3 min read • theVerge
Googles Pixel 10 Pro Fold is the first to go up in smoke during a bend test JerryRigEverything says