News
October 15, 2025 • 7 min read • theVerge
The best iPad deals you can get right now
October 15, 2025 • 1 min read • theVerge
The MLB apps best feature is a 30-second delay

October 15, 2025 • 1 min read • theVerge
Heres where you can preorder the new M5 MacBook Pro and iPad Pro

October 15, 2025 • 3 min read • theVerge
The iPad just got the chip it needs to be a smart home controller again
October 15, 2025 • 2 min read • theVerge
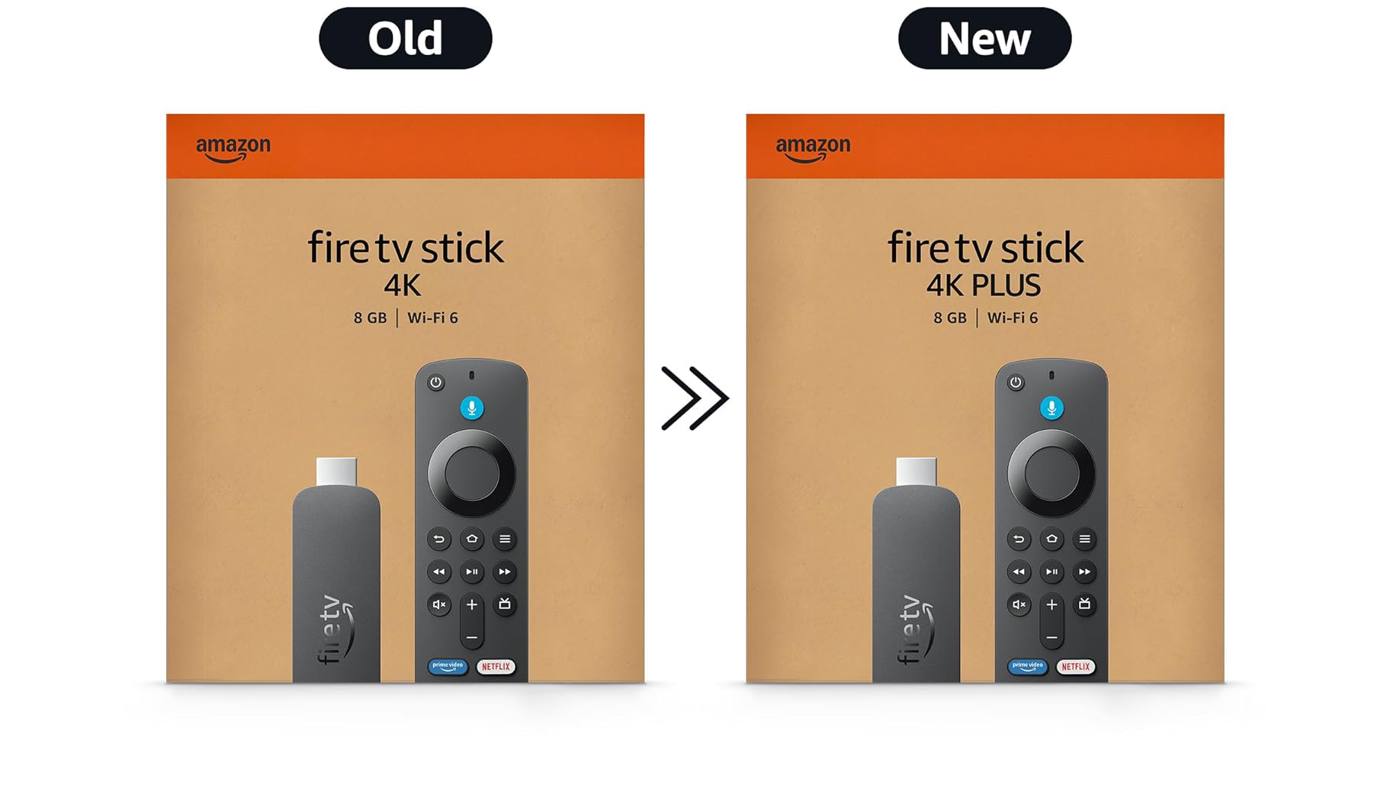
Amazons new name for the Fire TV Stick 4K only adds more confusion

October 15, 2025 • 1 min read • theVerge
New media is just right-wing media

October 15, 2025 • 1 min read • theVerge
I just reviewed the Xbox Ally ask me anything

October 15, 2025 • 3 min read • theVerge
Senate Democrats want to know was YouTubes Trump settlement a bribe
October 15, 2025 • 1 min read • Hackernews
Chinese Threat Group Jewelbug Quietly Infiltrated Russian IT Network for Months
A threat actor with ties to China has been attributed to a five-month-long intrusion targeting a Russian IT service provider, marking the hacking groups expansion to the country beyond Southeast Asia and South America. The activity, which took place from January to May 2025, has been attributed by Broadcom-owned Symantec to

October 15, 2025 • 1 min read • Hackernews
F5 Breach Exposes BIG-IP Source Code Nation-State Hackers Behind Massive Intrusion
U.S. cybersecurity company F5 on Wednesday disclosed that unidentified threat actors broke into its systems and stole files containing some of BIG-IPs source code and information related to undisclosed vulnerabilities in the product. It attributed the activity to a highly sophisticated nation-state threat actor, adding the adversary maintained long-term, persistent access