News

October 17, 2025 • 1 min read • Hackernews
Identity Security Your First and Last Line of Defense
The danger isn’t that AI agents have bad days — it’s that they never do. They execute faithfully, even when what they’re executing is a mistake. A single misstep in logic or access can turn flawless automation into a flawless catastrophe. This isnt some dystopian fantasy—its Tuesday at the office now.
October 17, 2025 • 1 min read • Hackernews
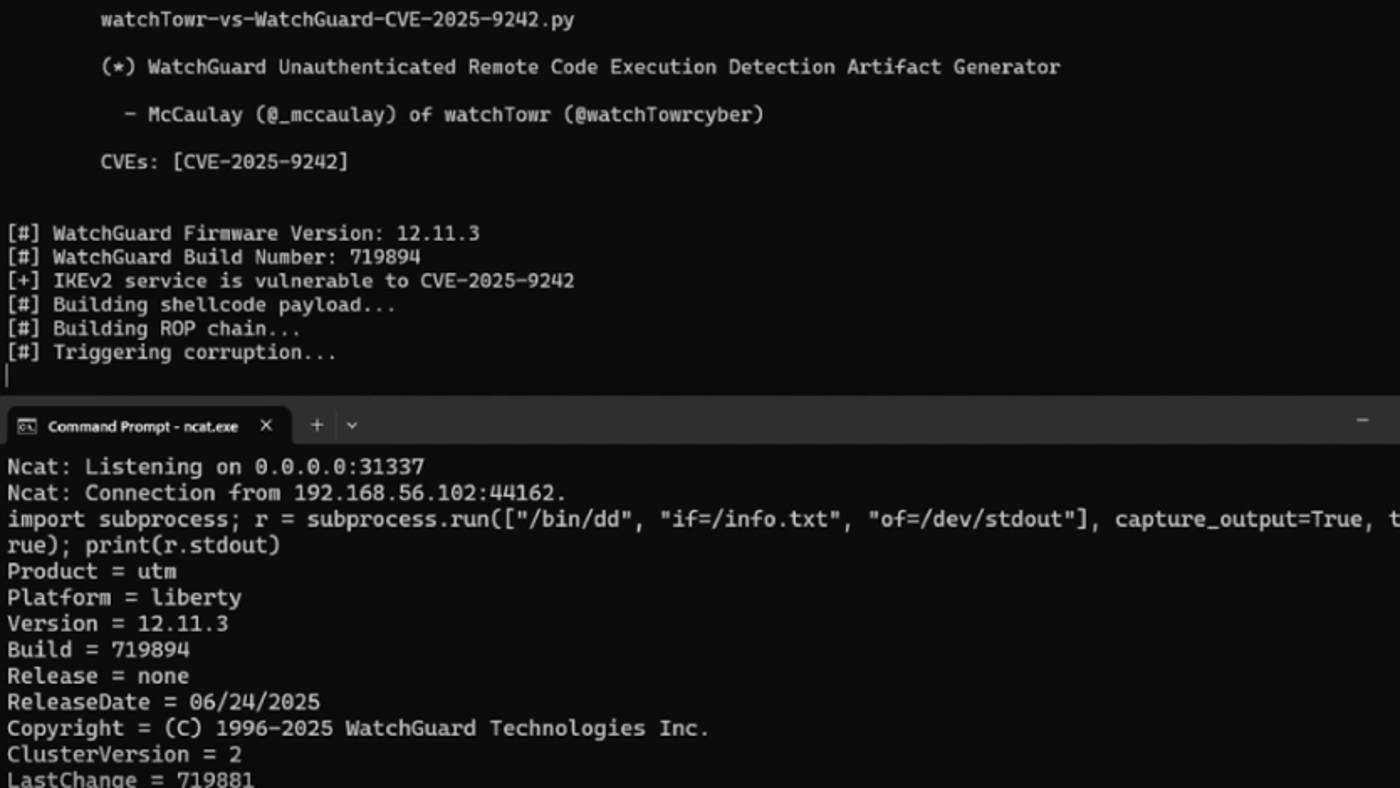
Researchers Uncover WatchGuard VPN Bug That Could Let Attackers Take Over Devices
Cybersecurity researchers have disclosed details of a recently patched critical security flaw in WatchGuard Fireware that could allow unauthenticated attackers to execute arbitrary code. The vulnerability, tracked as CVE-2025-9242 (CVSS score 9.3), is described as an out-of-bounds write vulnerability affecting Fireware OS 11.10.2 up to and including 11.12.4_Update1, 12.0 up to

October 17, 2025 • 2 min read • theVerge
Anthropic connects Claude to Microsoft Teams Outlook and OneDrive

October 17, 2025 • 1 min read • Hackernews
Microsoft Revokes 200 Fraudulent Certificates Used in Rhysida Ransomware Campaign
Microsoft on Thursday disclosed that it revoked more than 200 certificates used by a threat actor it tracks as Vanilla Tempest to fraudulently sign malicious binaries in ransomware attacks. The certificates were used in fake Teams setup files to deliver the Oyster backdoor and ultimately deploy Rhysida ransomware, the Microsoft Threat

October 16, 2025 • 15 min read • theVerge
The best laptop deals you can get right now

October 16, 2025 • 1 min read • theVerge
I just reviewed the Xbox Ally and answered your burning questions
October 16, 2025 • 2 min read • theVerge
OnePlus OxygenOS 16 brings Gemini into your Mind Space

October 16, 2025 • 1 min read • Hackernews
North Korean Hackers Use EtherHiding to Hide Malware Inside Blockchain Smart Contracts
A threat actor with ties to the Democratic Peoples Republic of Korea (aka North Korea) has been observed leveraging the EtherHiding technique to distribute malware and enable cryptocurrency theft, marking the first time a state-sponsored hacking group has embraced the method. The activity has been attributed by Google Threat Intelligence Group

October 16, 2025 • 1 min read • Hackernews
Hackers Abuse Blockchain Smart Contracts to Spread Malware via Infected WordPress Sites
A financially motivated threat actor codenamed UNC5142 has been observed abusing blockchain smart contracts as a way to facilitate the distribution of information stealers, such as Atomic (AMOS), Lumma, Rhadamanthys (aka RADTHIEF), and Vidar, targeting both Windows and Apple macOS systems. UNC5142 is characterized by its use of compromised WordPress websites
October 16, 2025 • 2 min read • theVerge
Google pitches Workspace tools for 8216when not if8217 Microsoft 365 fails