News
October 13, 2025 • 1 min read • Hackernews
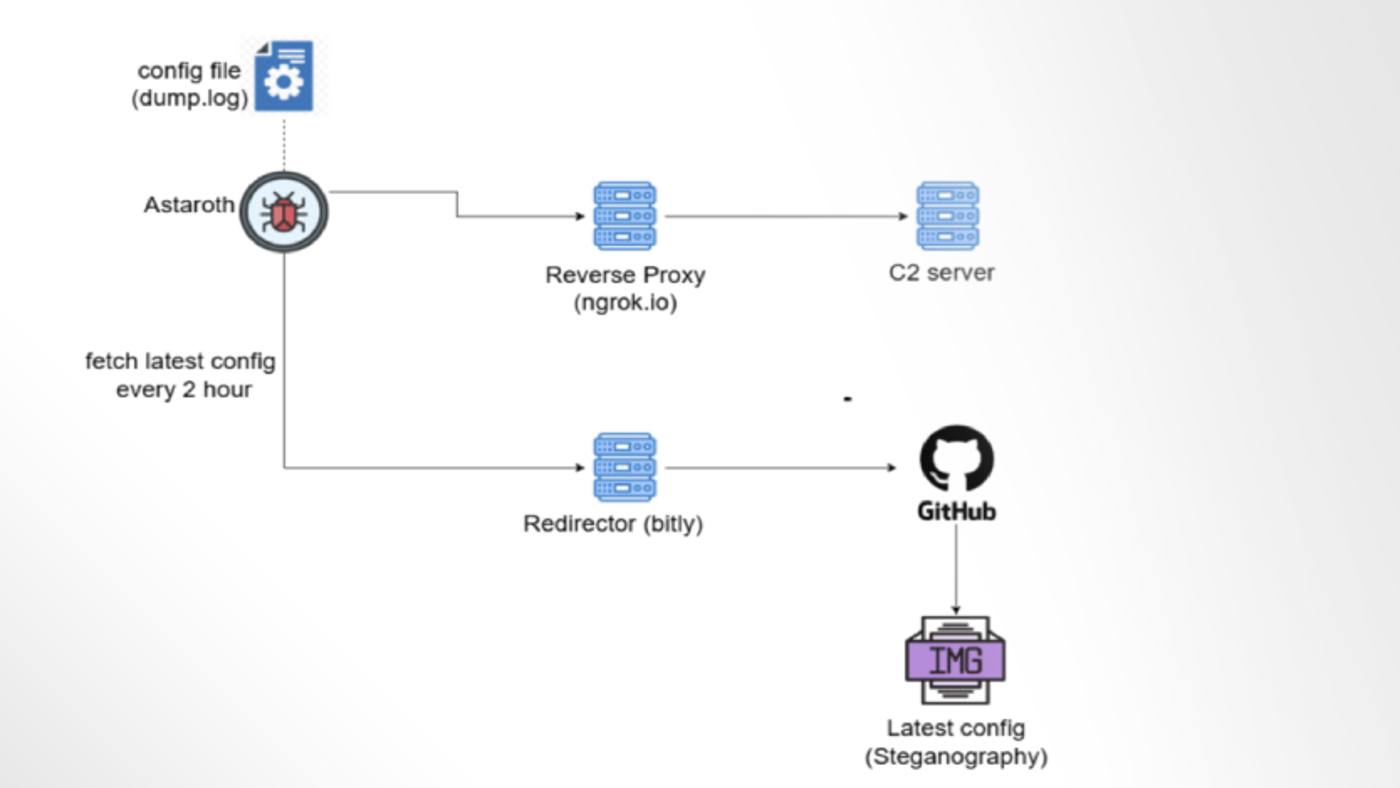
Astaroth Banking Trojan Abuses GitHub to Remain Operational After Takedowns
Cybersecurity researchers are calling attention to a new campaign that delivers the Astaroth banking trojan that employs GitHub as a backbone for its operations to stay resilient in the face of infrastructure takedowns. Instead of relying solely on traditional command-and-control (C2) servers that can be taken down, these attackers are leveraging

October 13, 2025 • 1 min read • Hackernews
New Rust-Based Malware ChaosBot Uses Discord Channels to Control Victims PCs
Cybersecurity researchers have disclosed details of a new Rust-based backdoor called ChaosBot that can allow operators to conduct reconnaissance and execute arbitrary commands on compromised hosts. Threat actors leveraged compromised credentials that mapped to both Cisco VPN and an over-privileged Active Directory account named, serviceaccount, eSentire said in a technical report

October 12, 2025 • 1 min read • Hackernews
New Oracle E-Business Suite Bug Could Let Hackers Access Data Without Login
Oracle on Saturday issued a security alert warning of a fresh security flaw impacting its E-Business Suite that it said could allow unauthorized access to sensitive data. The vulnerability, tracked as CVE-2025-61884, carries a CVSS score of 7.5, indicating high severity. It affects versions from 12.2.3 through 12.2.14. Easily exploitable vulnerability allows

October 11, 2025 • 1 min read • Hackernews
Experts Warn of Widespread SonicWall VPN Compromise Impacting Over 100 Accounts
Cybersecurity company Huntress on Friday warned of widespread compromise of SonicWall SSL VPN devices to access multiple customer environments. Threat actors are authenticating into multiple accounts rapidly across compromised devices, it said. The speed and scale of these attacks imply that the attackers appear to control valid credentials rather than brute-forcing. A

October 11, 2025 • 1 min read • Hackernews
Hackers Turn Velociraptor DFIR Tool Into Weapon in LockBit Ransomware Attacks
Threat actors are abusing Velociraptor, an open-source digital forensics and incident response (DFIR) tool, in connection with ransomware attacks likely orchestrated by Storm-2603 (aka CL-CRI-1040 or Gold Salem), which is known for deploying the Warlock and LockBit ransomware. The threat actors use of the security utility was documented by Sophos last

October 10, 2025 • 2 min read • theVerge
Chrome will automatically disable web notifications you dont care about

October 10, 2025 • 1 min read • Hackernews
Stealit Malware Abuses Nodejs Single Executable Feature via Game and VPN Installers
Cybersecurity researchers have disclosed details of an active malware campaign called Stealit that has leveraged Node.js Single Executable Application (SEA) feature as a way to distribute its payloads. According to Fortinet FortiGuard Labs, select iterations have also employed the open-source Electron framework to deliver the malware. Its assessed that the malware

October 10, 2025 • 1 min read • theVerge
You can now buy Microsoft8217s Windows XP Crocs for 7995

October 10, 2025 • 1 min read • Hackernews
Microsoft Warns of Payroll Pirates Hijacking HR SaaS Accounts to Steal Employee Salaries
A threat actor known as Storm-2657 has been observed hijacking employee accounts with the end goal of diverting salary payments to attacker-controlled accounts. Storm-2657 is actively targeting a range of U.S.-based organizations, particularly employees in sectors like higher education, to gain access to third-party human resources (HR) software as a service
October 10, 2025 • 1 min read • Hackernews
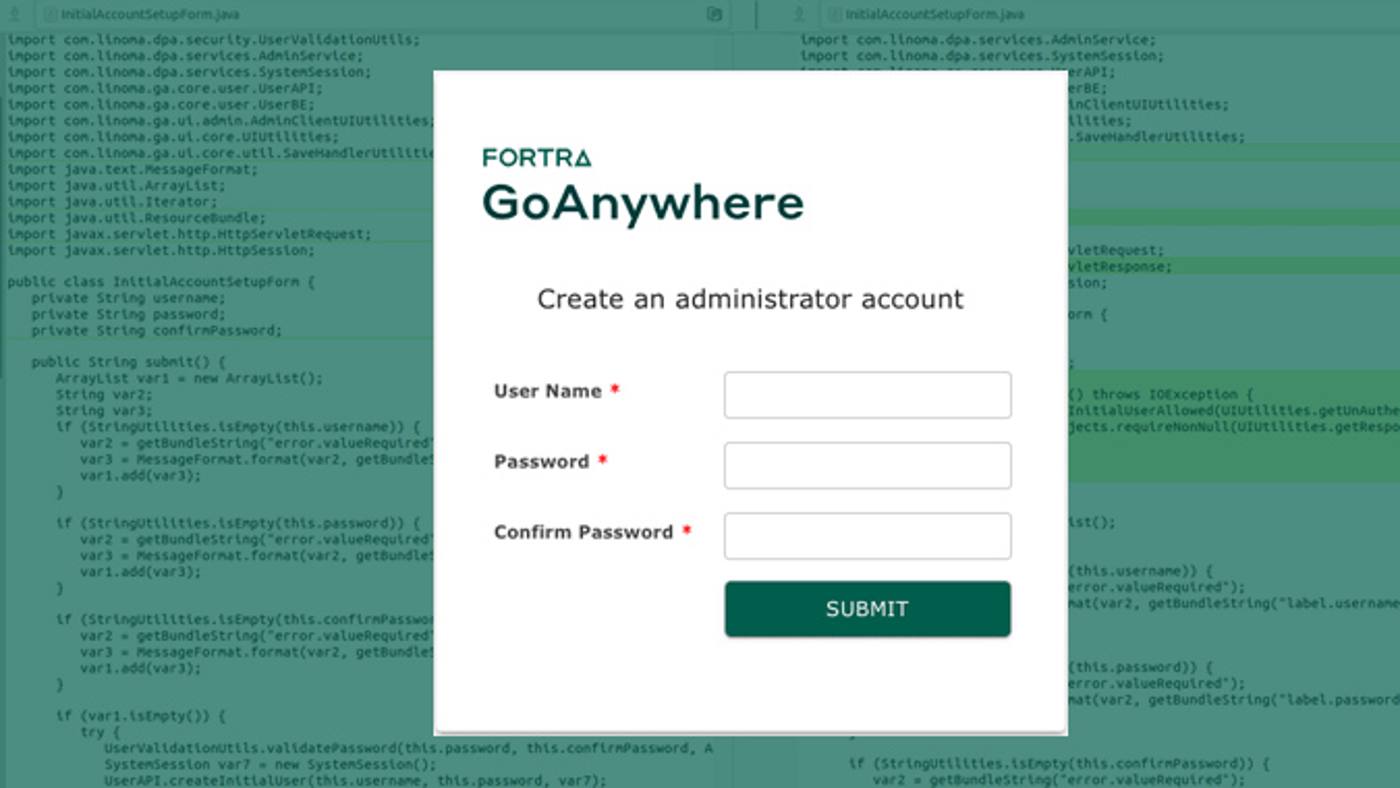
From Detection to Patch Fortra Reveals Full Timeline of CVE-2025-10035 Exploitation
Fortra on Thursday revealed the results of its investigation into CVE-2025-10035, a critical security flaw in GoAnywhere Managed File Transfer (MFT) thats assessed to have come under active exploitation since at least September 11, 2025. The company said it began its investigation on September 11 following a potential vulnerability reported by